1. a) Outline any three threats that a System Administrator may face as a result of networking computers.
b) Suggest any two measures that the system administrator can employ to reduce the network threats.
2. Study the data communication diagram below and answer the questions that follow:
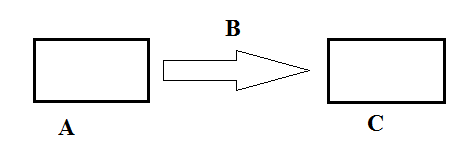
a) Name the elements of data communication labeled A, B and C.
b) Suggest the device used to connect A to B
c) State the protocol used to uniquely identify A and C
3. The table below consists of some of the peripheral devices of a computer.
Indicate Input or Output.
4. a) Give two reasons why an electronic spreadsheet application is suitable for preparing budgets.
b) State one use of each of the following applications;
i) Presentation software
ii) Word Processor
iii) Communication software
5. a) Name one example of presentation software.
b) Give the importance of each of the following features as used in electronic presentation;
i) Master Slide
ii) Transitions.
6. a) State three advantages of using e-mail services over sending mail by post.
b) State two advantages of post- mail services over e-mail communication.
7. Give five examples of networking hardware.
8. Outline five ways in which a student can use the Internet.
9. a) i) What is a data transmission media?
ii) Give two examples of transmission media.
b) Name two services offered by data communication tools.
10. a) Give any two services that use Electronic payment (E- payment) method.
b) State three advantages of using E – payments over traditional methods.
11. a) Name one tool used to remove dust from a computer.
b) Give reasons why one would require the following in the computer laboratory;
i) Uninterruptible Power Supply
ii) LCD projector
12. a) Write the procedure for changing the name of an existing file or folder.
b) Explain the function of a device driver in a computer system.
13. Write the following in full as used in Information and Communication Technology;
a) CCTV
b) ROM
c) CAD
d) CPU
e) VDU
14. a) Identify one storage device that is resistant to virus attacks.
b) Describe the following terms as used in computers;
i) File
ii) Folder
15. a) State four categories of the components of a computer system.
b) Give the function of any one category you have stated in 5(a).
16. Indicate TRUE or FALSE against each statement in the table below
|
STATEMENT |
TRUE/ FALSE |
|
| a) |
Open source software is copyrighted and distributed without costs for trial period. |
|
| b) |
Product activation is used to ensure that software is not installed illegally. |
|
| c) |
Programming software interfaces user application and computer hardware. |
|
| d) |
A file extension is a combination of characters used to identify a file |
|
| e) |
A clipboard holds copied data. |
17. a) Define the term hardware as used in Information and Communication Technology.
b) Name two ports used to connect devices on a computer.
c) Give one device that can be used to transfer a hardcopy document to a computer.
18. a) What is system software?
b) Outline any four functions of an operating system.
19. a) Distinguish between Reading and Writing in relation to storage medium.
b) Mention one example for each of the types of storage devices given below:
i) Optical storage
ii) Magnetic storage
iii) Solid state
20. a) Name any two examples of documents created using desktop publishing application.
b) State any three desktop publishing features that can enhance the documents you named in 10 (a).
